CCNA 200-301 Chapter 2 Network Access Lab 015 Configure and Verify Dynamic Trunk – DTP
Watch Full Demo on YouTube:
Lab Objective:
This lab aims to demonstrate the configuration of trunk ports dynamically to allow the passage of VLAN traffic between switches and devices, ensuring proper connectivity and efficient network segmentation.
Additionally, the objective includes verifying the trunk configuration to confirm correct VLAN propagation and ensure seamless communication between devices in different VLANs.
Through this lab, participants will gain practical experience in configuring and troubleshooting trunk links in a network topology comprising distribution and access layer switches.
Lab Topology:

Equipment Required:
- 2 x L3 Switches (e.g., WS-C3560-24PS-E)
- 2 x Cisco switch (e.g., WS-C2960-24TT-L)
- 4 x PCs or laptops with Ethernet ports (for data traffic)
- Console Cable
- Ethernet Cable for connections between devices
- Computer with Terminal emulation software e.g. PuTTY
IPv4 Address Table:
A. Switch VLAN Table:
| Device Name | Interface ID | Interface Mode | Allowed VLANs |
| Switch1 | GigabitEthernet0/1 | Trunk Auto | 10, 20 |
| Switch1 | GigabitEthernet0/2 | Trunk Auto | 10, 20 |
| Switch1 | Fa0/1 | Access | 10 |
| Switch1 | Fa0/2 | Access | 20 |
| Switch2 | GigabitEthernet0/1 | Trunk Auto | 10, 20 |
| Switch2 | GigabitEthernet0/2 | Trunk Auto | 10, 20 |
| Switch2 | Fa0/1 | Access | 10 |
| Switch2 | Fa0/2 | Access | 20 |
| Switch3 | GigabitEthernet0/1 | Trunk Desirable | 10, 20 |
| Switch3 | GigabitEthernet0/2 | Trunk Desirable | 10, 20 |
| Switch3 | Fa0/1 | Trunk Desirable | 10, 20 |
| Switch4 | GigabitEthernet0/1 | Trunk Desirable | 10, 20 |
| Switch4 | GigabitEthernet0/2 | Trunk Desirable | 10, 20 |
| Switch4 | Fa0/1 | Trunk Desirable | 10, 20 |
B. SVI Table:
| Device Name | Interface ID | IP Address | Subnet-Mask |
| Switch3 | VLAN 10 | 192.168.10.3 | 255.255.255.0 |
| Switch3 | VLAN 20 | 192.168.20.3 | 255.255.255.0 |
| Switch4 | VLAN 10 | 192.168.10.4 | 255.255.255.0 |
| Switch4 | VLAN 20 | 192.168.20.4 | 255.255.255.0 |
C. Hosts IP Address Table:
| Device Name | Interface ID | IPv4 Address | Subnet-Mask | VLAN | Default Gateway |
| PC1 | Fa0 | 192.168.10.10 | 255.255.255.0 | 10 | 192.168.10.3 |
| PC2 | Fa0 | 192.168.20.10 | 255.255.255.0 | 20 | 192.168.20.3 |
| PC3 | Fa0 | 192.168.10.11 | 255.255.255.0 | 10 | 192.168.10.4 |
| PC4 | Fa0 | 192.168.20.11 | 255.255.255.0 | 20 | 192.168.20.4 |
List of Command Summary:
| Command | Command Description |
| enable | enters privileged EXEC mode. |
| configure terminal | enters global configuration mode from privileged EXEC mode. |
| hostname [hostname] | assign a device name to router. |
| switchport mode trunk | is used to configure an interface on a Cisco switch to operate in trunk mode. In trunk mode, the interface is capable of carrying traffic for multiple VLANs simultaneously. This command allows the interface to send and receive traffic with VLAN tags, enabling it to interconnect switches or routers and carry traffic for multiple VLANs across a single link. |
| switchport trunk allowed vlan ID | is used to specify which VLANs are allowed to traverse a trunk port on a Cisco switch. By default, all VLANs are allowed on a trunk port. However, this command can be used to restrict the VLANs that are permitted to pass through the trunk link. You can specify individual VLAN IDs or specify a range of VLAN IDs that are permitted on the trunk port. |
| show interfaces [interface-ID] switchport | is used to display detailed information about the switchport configuration of a specific interface on a Cisco switch. It provides information such as the administrative and operational mode of the switchport, the VLAN membership of the switchport, trunking status, allowed VLANs, native VLAN, and other relevant details related to the switchport configuration. |
| show interfaces trunk | displays information about trunk interfaces and their associated VLANs. It provides details about which interfaces are configured as trunk links, the encapsulation type (such as dot1Q), the operational status of the trunk, the allowed VLANs on the trunk, and the native VLAN. This command is useful for verifying trunk configurations and troubleshooting trunking issues on Cisco switches. |
| vlan [vlan-id] | used to create a new VLAN with the specified VLAN ID. This command allows network administrators to segment the network into multiple virtual LANs (VLANs) for better traffic management and security. By assigning devices to different VLANs based on their network requirements, administrators can control broadcast domains, enforce security policies, and optimize network performance. |
| switchport mode access | used on Cisco switches to configure an interface as an access port. Access ports are used to connect end devices, such as computers or printers, to the switch. When configured as an access port, the switch treats all incoming frames on that interface as belonging to the VLAN assigned to the port. This command disables dynamic trunking protocol (DTP) negotiation on the interface, ensuring that it operates only as an access port and does not participate in VLAN trunking. |
| switchport access vlan [VLAN-ID] | used on Cisco switches to assign a specific VLAN to an access port. This command is typically used in conjunction with the “switchport mode access” command to configure an interface as an access port and specify the VLAN to which it belongs. By assigning a VLAN to an access port, the switch ensures that all incoming traffic on that port is tagged with the specified VLAN ID. This allows the switch to segregate traffic from different VLANs and control broadcast and multicast traffic within each VLAN. |
| switchport voice vlan [vlan-id] | used in Cisco switch interfaces to configure the Voice VLAN assignment. When applied to an interface, it designates a specific VLAN ID for voice traffic, allowing the switch to separate voice and data traffic on the same physical interface. This command ensures that voice traffic is tagged with the specified VLAN ID when transmitted over the network |
| switchport mode dynamic auto | allows the interface to dynamically negotiate trunking with the neighboring device, becoming a trunk port if the other end initiates trunk negotiation. |
| switchport mode dynamic desirable | configures the interface to actively negotiate trunking with the neighboring device, becoming a trunk port if the other end supports trunking. |
| switchport trunk encapsulation dot1q | used to configure the encapsulation method for a trunk port on a Cisco switch. Specifically, it specifies that the switch should use the IEEE 802.1Q encapsulation protocol for tagging VLAN information on frames traversing the trunk port. This command is typically applied to a port configured as a trunk port using the “switchport mode trunk” command. By default, Cisco switches use the 802.1Q encapsulation method for trunk ports, so this command is often unnecessary unless there is a specific requirement to explicitly set the encapsulation method |
| show vlan brief | used on Cisco switches to display a summary of VLAN information. When you enter this command in the CLI interface of a Cisco switch, it provides a concise overview of the VLAN configuration on the switch. This includes details such as the VLAN ID, name, and interface membership status. The output of this command is often used to quickly verify the VLAN configuration and interface assignments on the switch. |
| ipconfig /all | used in Windows operating systems to display detailed information about all network interfaces and their configurations. |
| no shutdown | enables an interface. |
| show running-config | save the running configuration to the startup-configuration file. |
| show running-config | section interface GigabitEthernet0/* | used to display the configuration details of a specific GigabitEthernet interface (interface GigabitEthernet0/) within the running configuration of a Cisco device. This command allows you to view the configuration settings related to the specified interface only, filtering out other configuration sections. It provides a focused view of the configuration parameters associated with the specified interface, including its IP address, VLAN membership, trunking settings, and any other relevant configuration details. The asterisk (*) is a wildcard character that matches any character or sequence of characters. In this context, it is used to match any subinterface under GigabitEthernet0. |
| show running-config | section interface FastEthernet0/1$ | The “show running-config | section interface FastEthernet0/1$” command is similar to the previous one, but it focuses specifically on the FastEthernet0/1 interface. The “$” symbol at the end of the interface name indicates that the command will match only the interface that ends with “FastEthernet0/1”. This command is helpful when you want to view the configuration details of a specific FastEthernet interface without displaying configurations for other interfaces. |
| copy running-config startup-config | used to save the currently running configuration (stored in the RAM) to the startup configuration (stored in the NVRAM) |
| end | exit configuration mode. |
| exit | exits one level in the menu structure command. |
Lab Task:
- Connect the devices according to the provided topology.
- Connect to the CLI of all switches and enable privileged EXEC mode and go to configuration mode. Configure the appropriate hostname on each device as per topology shown above.
- VLAN and SVI Configurations:
- On Switch1:
- Create VLAN 10 and 20
- Name each VLAN with the appropriate department
- Verify the configuration above
- On Switch2:
- Create VLAN 10 and 20
- Name each VLAN with the appropriate department
- Verify the configuration above
- On Switch3:
- Create VLAN 10 and 20
- Name each VLAN with the appropriate department
- Verify the configuration above
- Configure the SVI as shown in the SVI Table above
- Verify the SVI configuration
- On Switch4:
- Create VLAN 10 and 20
- Name each VLAN with the appropriate department
- Verify the configuration above
- Configure the SVI as shown in the SVI Table above
- Verify the SVI configuration
- On Switch1:
- Trunk Configuration:
- On Switch1 and Switch2 do the following:
- On Interface GigabitEthernet0/1 and GigabitEthernet0/2, configure the following:
- Configure both interfaces to use dynamic trunking using the auto option
- Set the allowed VLANs only to VLANs 10 and 20
- Set the interface description to include which device is connected to
- Verify Trunk configurations and check the admin operation of the interface
- Set the native VLAN to 10
- Verify the native VLAN
- On Interface GigabitEthernet0/1 and GigabitEthernet0/2, configure the following:
- On Switch3 and Switch4:
- On Interface FastEthernet0/1, GigabitEthernet0/1 and GigabitEthernet0/2, configure the following:
- Set the trunk encapsulation to use 802.1q
- Configure both interfaces to use dynamic trunking using the desirable option
- Set the allowed VLANs only to VLANs 10 and 20
- Set the interface description to include which device is connected to
- Verify Trunk configurations and check the admin operation of the interface
- Set the native VLAN to 10
- Verify the native VLAN
- On Interface FastEthernet0/1, GigabitEthernet0/1 and GigabitEthernet0/2, configure the following:
- On Switch1 and Switch2 do the following:
- Access port configuration:
- On Switch1 and Switch2:
- Assign Fa0/1 and Fa0/2 interfaces with the appropriate VLAN Access, include an interface description as per department and force each port to operate in access mode
- Verify the step above with the appropriate command
- On Switch1 and Switch2:
- End host configuration:
- Configure the appropriate IP address on each PC from each department
- Verify that each PC has the appropriate IP address
- Connectivity test between devices within the same VLAN:
- Ping from PC1 to PC3, is the ping successful?
- Ping from PC2 to PC4, is the ping successful?
- Test Inter-VLAN communications:
- Ping from PC1 to PC4, is the ping successful? Why?
- On Switch3 and Switch4, enable IP Routing and repeat step 8.
- If the ping is successful then go ahead and save the configuration. Else, use the troubleshoot steps below:
- Check VLAN configuration on each Switch
- Verify each port assignments to the VLAN in question
- Ensure Trunk links are properly configured
- Verify IP addressing and routing if applicable
Lab Solution:
1. Lab has been created:
2. To configure the hostname on each Switch you can following the commands below:
a. On Switch1:
Switch>enable
Switch#configure terminal
Switch(config)#hostname Switch1
Switch1(config)#
b. On Switch2:
Switch>enable
Switch#configure terminal
Switch(config)#hostname Switch2
Switch2(config)#
c. On Switch3:
Switch>enable
Switch#configure terminal
Switch(config)#hostname Switch3
Switch3(config)#
d. On Switch4:
Switch>enable
Switch#configure terminal
Switch(config)#hostname Switch4
Switch4(config)#
3. VLAN and SVI Configurations:
a. On Switch1:
Configure VLANs 10, 20:
Switch1(config)# vlan 10
Switch1(config-vlan)# name IT_Department
Switch1(config-vlan)# vlan 20
Switch1(config-vlan)# name HR_Department
Verification/inflight checks:

b. On Switch2:
Configure VLANs 10, 20:
Switch2(config)# vlan 10
Switch2(config-vlan)# name IT_Department
Switch2(config-vlan)# vlan 20
Switch2(config-vlan)# name HR_Department
Verification/inflight checks:

c. On Switch3:
Configure VLANs 10, 20:
Switch3(config)# vlan 10
Switch3(config-vlan)# name IT_Department
Switch3(config-vlan)# vlan 20
Switch3(config-vlan)# name HR_Department
Verification/inflight checks: “show vlan brief”
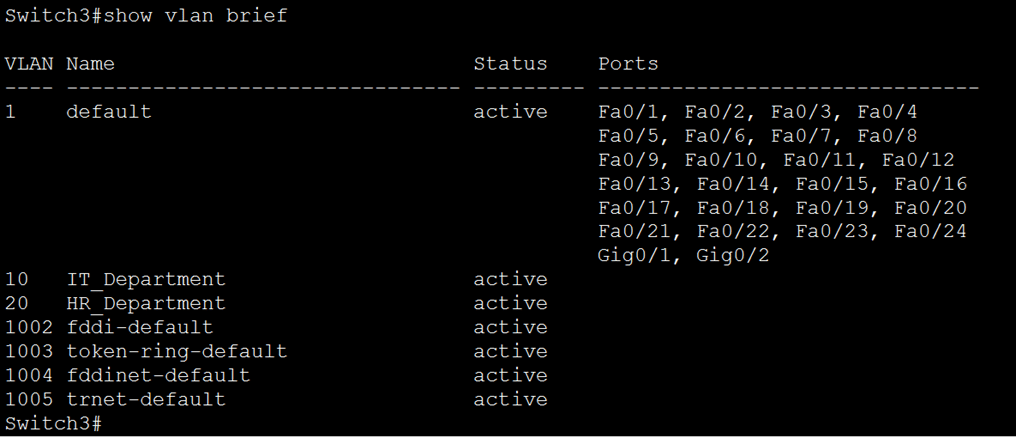
SVI Configuration for VLAN 10 and 20:
Switch3(config)#interface vlan 10
Switch3(config-if)#
%LINK-5-CHANGED: Interface Vlan10, changed state to up
Switch3(config-if)#ip address 192.168.10.3 255.255.255.0
Switch3(config-if)#interface vlan 20
%LINK-5-CHANGED: Interface Vlan20, changed state to up
Switch3(config-if)#ip address 192.168.20.3 255.255.255.0
Switch3(config-if)#end
Switch3#
Verification/inflight checks: “show ip interface brief | include lan”

d. On Switch4:
Configure VLANs 10, 20:
Switch4(config)# vlan 10
Switch4(config-vlan)# name IT_Department
Switch4(config-vlan)# vlan 20
Switch4(config-vlan)# name HR_Department
Verification/inflight checks:

SVI Configuration for VLAN 10 and 20:
Switch4(config)#interface vlan 10
Switch4(config-if)#
%LINK-5-CHANGED: Interface Vlan10, changed state to up
Switch4(config-if)#ip address 192.168.10.4 255.255.255.0
Switch4(config-if)#interface vlan 20
%LINK-5-CHANGED: Interface Vlan20, changed state to up
Switch4(config-if)#ip address 192.168.20.4 255.255.255.0
Switch4(config-if)#end
Switch4#
Verification/inflight checks: “show ip interface brief | include lan”

4. Trunk Configuration:
a. On Switch1 and Switch2:
On Interface GigabitEthernet0/1 and GigabitEthernet0/2:
Switch1(config)#interface range gigabitEthernet 0/1-2
Switch1(config-if-range)#switchport mode dynamic auto
Switch1(config-if-range)#switchport trunk allowed vlan 10,20
Switch1(config-if-range)#description “Link to Distrubtion Switch”
Switch1(config-if-range)#end
Switch1#
Switch2(config)#interface range gigabitEthernet 0/1-2
Switch2(config-if-range)#switchport mode dynamic auto
Switch2(config-if-range)#switchport trunk allowed vlan 10,20
Switch2(config-if-range)#description “Link to Distrubtion Switch”
Switch2(config-if-range)#end
Switch2#
Verification/inflight checks: “show interfaces trunk”

You can see from the screenshot above that there is no output from the “show interfaces trunk”. This is because the interface still operating in access mode. This is because the “switch mode dynamic auto” command will not initiate trunk negotiation. So it will only become a Trunk port if the neighnoring device initiated Trunk negotiation. This can be done if the other side of the link is configured with this command “switch mode dynamic desirable”.
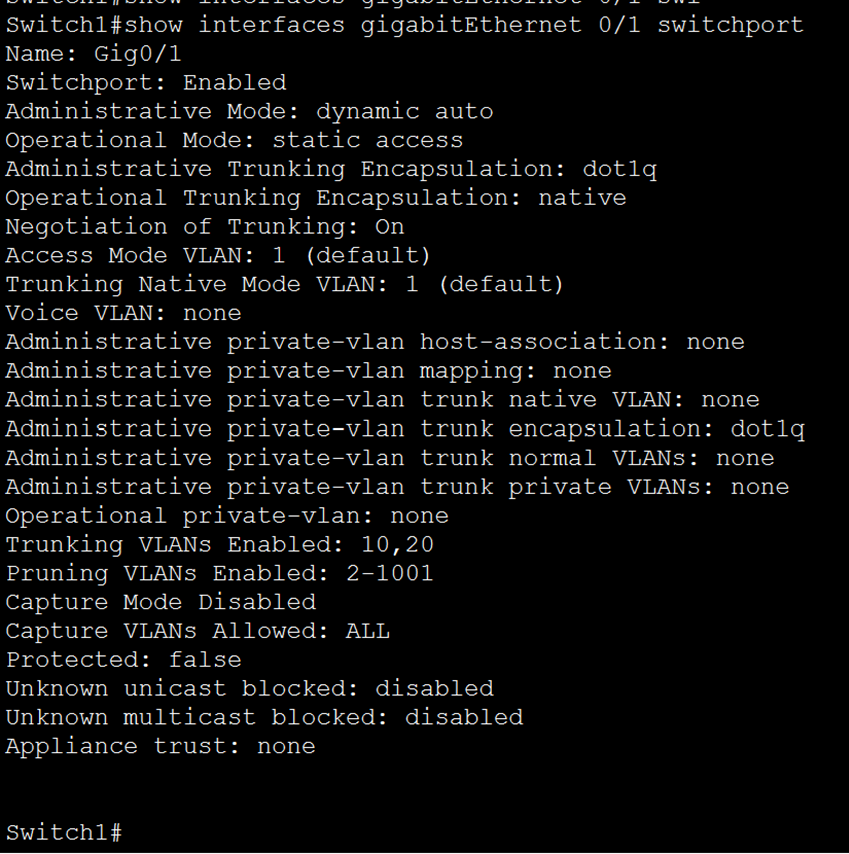
You can see from the output above that the current operation mode is set to Access.


On Interface GigabitEthernet0/1 and GigabitEthernet0/2, change the native VLAN from 1 to 10:
Switch1(config)#interface range gigabitEthernet 0/1-2
Switch1(config-if-range)# switchport trunk native vlan 10
Switch2(config)#interface range gigabitEthernet 0/1-2
Switch2(config-if-range)# switchport trunk native vlan 10
Verification/inflight checks: “show running-config | section interface GigabitEthernet0/*”

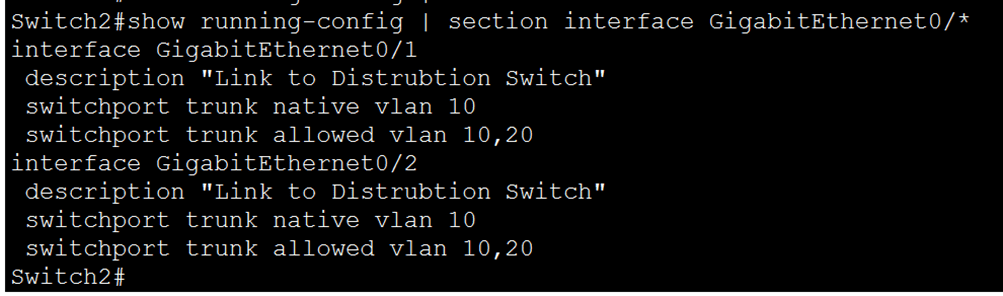
b. On Switch3 and Switch4:
On Interface GigabitEthernet0/1 and GigabitEthernet0/2 and FastEthernet0/1:
Switch3(config)# interface range gigabitEthernet 0/1-2, fastEthernet 0/1
Switch3(config-if-range)#switchport trunk encapsulation dot1q
Switch3(config-if-range)#switchport mode dynamic desirable
Switch3(config-if-range)#switchport trunk allowed vlan 10,20
Switch3(config-if-range)#interface range gigabitEthernet 0/1-2
Switch3(config-if-range)#description “Link to Access Switches”
Switch3(config-if-range)#inter fa 0/1
Switch3(config-if)#description ” Link to Distribution Switch4″
Switch3(config-if)#
Switch3#
Switch4(config)# interface range gigabitEthernet 0/1-2, fastEthernet 0/1
Switch4(config-if-range)#switchport trunk encapsulation dot1q
Switch4(config-if-range)#switchport mode dynamic desirable
Switch4(config-if-range)#switchport trunk allowed vlan 10,20
Switch4(config-if-range)#interface range gigabitEthernet 0/1-2
Switch4(config-if-range)#description “Link to Access Switches”
Switch4(config-if-range)#inter fa 0/1
Switch4(config-if)#description ” Link to Distribution Switch3″
Switch4(config-if)#
Switch4#
Verification/inflight checks: “show interfaces trunk”


Issue this command as well “show running-config | section interface FastEthernet0/1$”:


On Interface GigabitEthernet0/1 and GigabitEthernet0/2 and FastEthernet0/1, set the native VLAN to 10:
Switch3(config)# interface range gigabitEthernet 0/1-2, fastEthernet 0/1
Switch3(config-if-range)#switchport trunk native vlan 10
Switch4(config)# interface range gigabitEthernet 0/1-2, fastEthernet 0/1
Switch4(config-if-range)# switchport trunk native vlan 10
Verification/inflight checks: “show interfaces trunk”

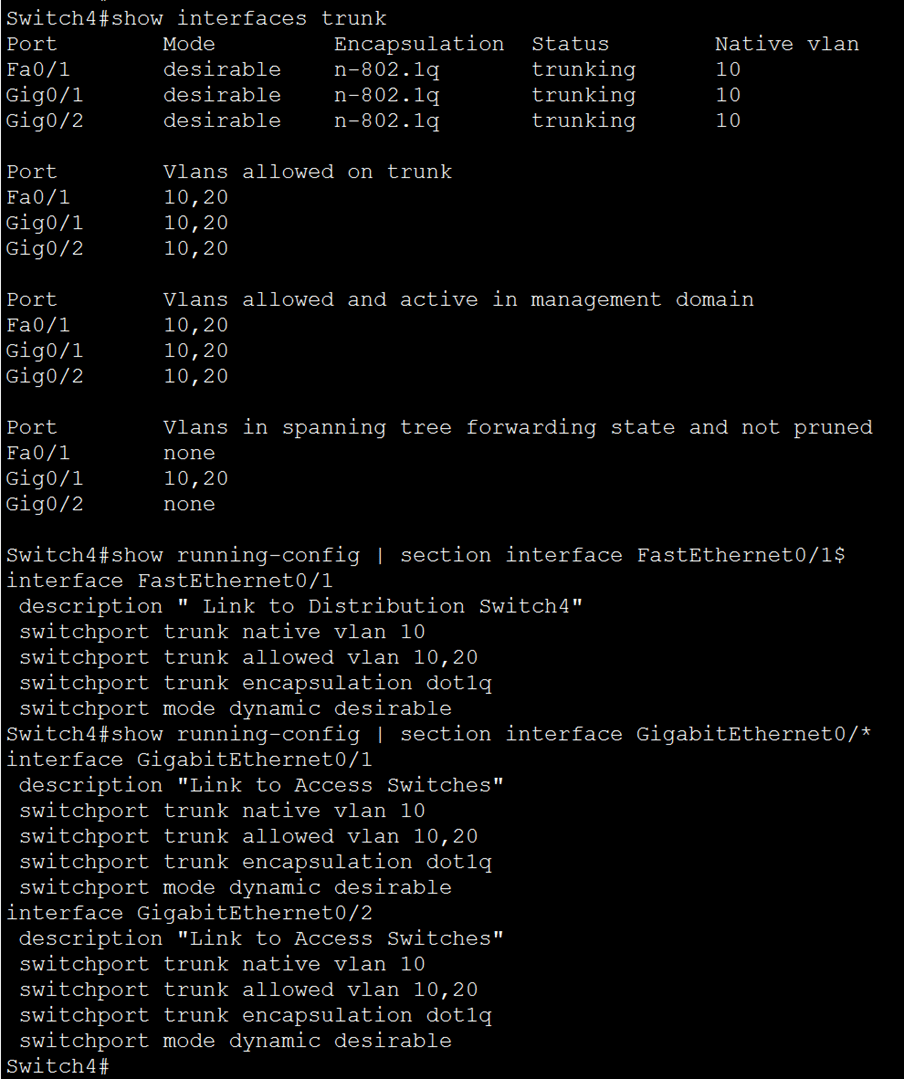
5. Access port configuration:
a. On Switch1 and Switch2:
Switch1(config-if-range)#interface fast 0/1
Switch1(config-if)#switchport mode access
Switch1(config-if)#switchport access vlan 10
Switch1(config-if)#description “Link to PC1”
Switch1(config-if)#interface fast 0/2
Switch1(config-if)#switchport mode access
Switch1(config-if)#switchport access vlan 20
Switch1(config-if)#description “Link to PC2”
Switch2(config-if-range)#interface fast 0/1
Switch2(config-if)#switchport mode access
Switch2(config-if)#switchport access vlan 10
Switch2(config-if)#description “Link to PC3”
Switch2(config-if)#interface fast 0/2
Switch2(config-if)#switchport mode access
Switch2(config-if)#switchport access vlan 20
Switch2(config-if)#description “Link to PC4”
Verification/inflight checks: “show vlan brief”






6. End host configuration:
Configure each PC according to the IPv4 address table:

7. Connectivity test between devices within the same VLAN:
a. Ping from PC1 to PC3, is the ping successful?: Yes it is, see screenshot below:


8. Test Inter-VLAN communications:
a. Ping from PC1 to PC4, is the ping successful? Why?
Ping has failed due to routing not being enabled on both distribution layer Switches. When the “ip routing” command is not enabled on a Cisco layer 3 switch, the switch operates in layer 2 mode, meaning it forwards traffic based solely on MAC addresses and does not perform routing between VLANs. As a result, there is no communication between different VLANs because the switch does not have the capability to route traffic between them.
Enabling the “ip routing” command turns the layer 3 switch into a router, allowing it to perform inter-VLAN routing. With this command enabled, the switch can route traffic between different VLANs based on their IP addresses, thus enabling communication between devices in different VLANs.

19. On Switch3 and Switch4, enable IP Routing and repeat step 8:
Configure IP Routing on both distribution Switches:
Switch3#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch3(config)#ip routing
Switch4#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch4(config)#ip routing
Repeat Step 8, where we check connectivity between PC1 and PC4:

10. Save the configuration by issuing either “wr” or “copy running-config startup-config” command on all Cisco devices.
Troubleshooting:
- Physical Connectivity Check:
- Verify that all cables are securely connected to the correct ports on the switches.
- Ensure that the devices in the access layer are connected to the correct VLAN ports.
- Trunk Configuration Check:
- Verify that the trunk ports on the distribution layer switches are configured correctly.
- Check the trunk encapsulation method (dot1Q) and ensure consistency on both ends of the trunk link.
- VLAN Configuration Check:
- Verify that the VLANs are configured identically on both switches.
- Ensure that the VLANs allowed on the trunk links match on both switches.
- Interface Status Check:
- Use the “show interface” command to check the status of the trunk ports.
- Look for any errors or issues such as interface down, errors, or congestion.
- VLAN Membership Check:
- Use the “show vlan brief” command to verify VLAN membership on each switch.
- Ensure that the VLANs required for trunking are active and correctly configured.
- Trunk Negotiation Check:
- If the trunk link is configured for dynamic negotiation (DTP), ensure that both ends are set to the same negotiation mode.
- Verify that DTP negotiation is successful and that the trunk link is established.
- Traffic Testing:
- Attempt to send traffic between devices in different VLANs.
- Use tools like ping or traceroute to verify connectivity.
- Check for any packet loss or latency.
- Debugging Commands:
- Utilize debugging commands such as “debug trunk”, “debug vlan”, or “debug interface” to gather more detailed information about trunking and VLAN issues.
- Be cautious when using debugging commands in a production environment, as they can impact performance.
- Review Configuration Changes:
- Check recent configuration changes to identify any potential misconfigurations or unintended changes that may have caused the issue.
- Documentation and Documentation Review:
- Review network documentation to ensure that configurations align with design requirements and best practices.
- Document any troubleshooting steps taken and their outcomes for future reference.
Note:
A trunk refers to a communication link that carries multiple VLANs (Virtual Local Area Networks) between switches, routers, or other network devices. Trunks are essential for efficiently managing and segregating network traffic, especially in environments where multiple VLANs are used to segment traffic for security, performance, or organizational reasons.
Here are the key aspects and functionalities of trunks in IT networking:
- Carrying Multiple VLANs:
- Trunks enable the transportation of traffic from multiple VLANs over a single physical or logical link. This allows different VLANs to communicate with each other across the network.
- 802.1Q VLAN Tagging:
- Trunks typically use the IEEE 802.1Q standard for VLAN tagging. Each Ethernet frame traveling over the trunk is tagged with a VLAN identifier (VLAN ID), allowing switches to differentiate between different VLANs.
- Encapsulation:
- Trunks encapsulate Ethernet frames with VLAN tags to distinguish traffic belonging to different VLANs. This process is known as VLAN encapsulation, and it ensures that traffic remains segregated and identifiable as it traverses the trunk link.
- Dynamic Trunking Protocol (DTP):
- DTP is a Cisco proprietary protocol that facilitates automatic negotiation of trunk links between switches. DTP-enabled switches exchange messages to dynamically establish trunk links and negotiate trunking parameters such as encapsulation method (e.g., dot1Q).
- Static Trunk Configuration:
- Alternatively, trunk links can be manually configured on network devices using specific commands to specify trunking parameters such as encapsulation method and allowed VLANs. Static trunk configuration provides more control and predictability but requires manual configuration.
- VLAN Tagging and Untagging:
- Trunks carry VLAN-tagged traffic between switches. When traffic exits a trunk link and enters an access port connected to an end device (e.g., a computer or IP phone), the VLAN tags are removed in a process known as VLAN untagging or VLAN stripping.
- Inter-VLAN Routing:
- Trunks play a crucial role in enabling inter-VLAN communication. By carrying traffic from multiple VLANs, trunks allow routers or layer 3 switches to perform inter-VLAN routing, facilitating communication between devices on different VLANs.
- Bandwidth Efficiency:
- Trunks help optimize network bandwidth by consolidating multiple VLANs onto a single link. This reduces the number of physical connections required between switches and minimizes network complexity.
Overall, trunks are fundamental components of modern network architectures, enabling efficient and flexible communication between VLANs while ensuring traffic segregation and optimal resource utilization. Understanding trunking concepts and configurations is essential for network administrators and engineers responsible for designing, deploying, and managing enterprise networks.
Tips:
| SW1 SW2 | Trunk | Access | Dynamic Desirable | Dynamic Auto |
| Trunk | T | X | T | T |
| Access | X | A | A | A |
| Dynamic Desirable | T | A | T | T |
| Dynamic Auto | T | A | T | A |
T = Trunk
A = Access
X = None
Conclusion:
In conclusion, configuring and verifying dynamic trunks is essential for ensuring efficient communication between VLANs in a network environment. By establishing trunk links between switches and properly configuring trunking parameters such as encapsulation method and allowed VLANs, network administrators can facilitate seamless traffic flow across VLANs while maintaining network segmentation and security.
Through this lab, we have gained valuable hands-on experience in configuring and verifying dynamic trunks, allowing us to understand the importance of trunking in modern network architectures. By troubleshooting any issues that arise during the configuration process, we have honed our troubleshooting skills and deepened our understanding of trunking concepts.
Moving forward, this knowledge will be invaluable as we continue to design, deploy, and manage complex network infrastructures. Whether it’s optimizing bandwidth usage, enabling inter-VLAN communication, or supporting dynamic network growth, the ability to configure and verify dynamic trunks is a crucial skill for any network professional.
By mastering the concepts covered in this lab, we are better equipped to tackle the challenges of modern networking and contribute to the efficiency and reliability of our network environments.
Packet Tracer Lab (Pre/Post configuration):
Download the file below and open the word document to access the Packet Tracer labs.