Lab 008 Practice VLSM – RFC1918 – Class C
Watch Full Demo on YouTube:
Lab Objective:
The main objective of this lab is to gain practical experience in verifying Address Resolution Protocol (ARP) operations within a network environment.
Through this exercise, we aim to understand how ARP facilitates the mapping of IP addresses to MAC addresses, enabling devices
to communicate effectively on the same local network segment. Additionally, we seek to explore the dynamic nature of ARP cache entries and troubleshoot any issues related to ARP resolution.
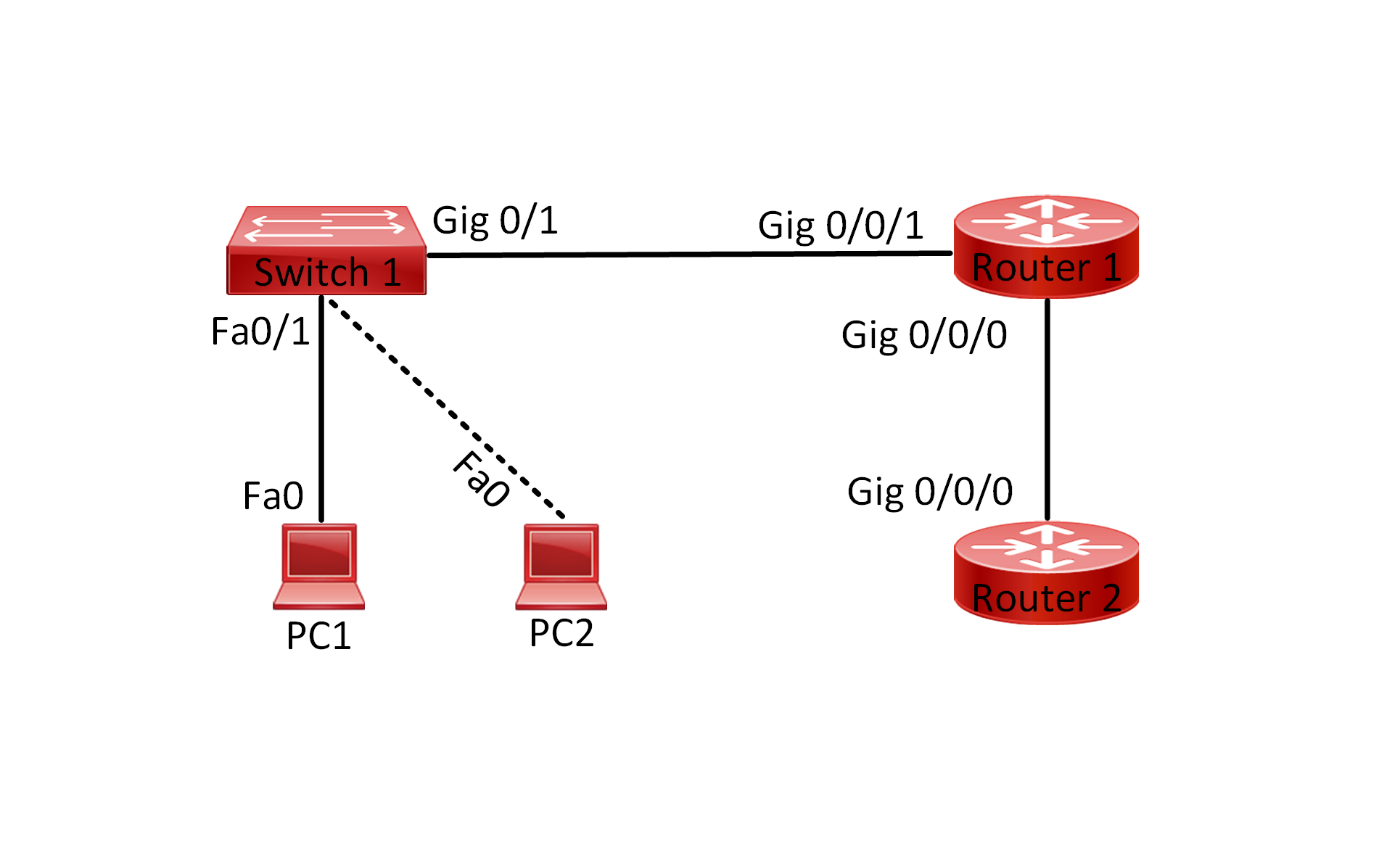
Lab Topology:

Equipment Required:
- 1x Cisco router (e.g., Cisco ISR series)
- 1x Cisco switch (e.g., Cisco Catalyst series)
- 12x PCs or laptops with Ethernet ports
- Console Cable
- Ethernet Cable for connections between devices
- Computer with Terminal emulation software e.g. PuTTY
IPv4 Address Table:
A. Router IP Address Table:
| Device Name | Interface ID | IPv4 Address | Subnet-Mask | dot1Q |
| Router1 | Loopback100 | 8.8.8.8 | 255.255.255.255 | N/A |
| Router1 | GigabitEthernet0/0/0.100 | 100 | ||
| Router1 | GigabitEthernet0/0/0.200 | 200 | ||
| Router1 | GigabitEthernet0/0/0.300 | 300 | ||
| Router1 | GigabitEthernet0/0/0.400 | 400 | ||
| Router1 | GigabitEthernet0/0/0.500 | 500 | ||
| Router1 | GigabitEthernet0/0/0.600 | 600 |
B. Switches IP Address Table:
| Device Name | Interface ID | Port Mode | VLAN |
| Switch1 | GigabitEthernet0/1 | Trunk | 100,200,300,400,500,600 |
| Switch1 | Fa0/1-2 | Access | 100 |
| Switch1 | Fa0/3-4 | Access | 200 |
| Switch1 | Fa0/5-6 | Access | 300 |
| Switch1 | Fa0/7-8 | Access | 400 |
| Switch1 | Fa0/9-10 | Access | 500 |
| Switch1 | Fa0/11-12 | Access | 600 |
C. Hosts IP Address Table:
| Device Name | Department | Interface ID | IPv4 Address | Subnet-Mask | Default Gateway | CIDR Notation |
| PC1 | Engineering | Fa0 | ||||
| PC2 | Engineering | Fa0 | ||||
| PC3 | HR | Fa0 | ||||
| PC4 | HR | Fa0 | ||||
| PC5 | IT | Fa0 | ||||
| PC6 | IT | Fa0 | ||||
| PC7 | Production | Fa0 | ||||
| PC8 | Production | Fa0 | ||||
| PC9 | Finance | Fa0 | ||||
| PC10 | Finance | Fa0 | ||||
| PC11 | Distribution | Fa0 | ||||
| PC12 | Distribution | Fa0 |
List of Command Summary:
| Command | Command Description |
| enable | enters privileged EXEC mode. |
| configure terminal | enters global configuration mode from privileged EXEC mode. |
| hostname [hostname] | assign a device name to router. |
| interface loopback [id] | this command allows you to configure a virtual interface with a specific ID (number) for various purposes such as testing, management, or routing protocols. The loopback interface is always up and can be used to provide a stable IP address for services, advertise router IDs in routing protocols, or simulate network presence without the need for physical interfaces. |
| interface [type number] | change from global configuration mode to interface configuration mode. |
| interface [type number].[sub-interface-id] | used to create a sub-interface. This command allows you to configure settings specific to this sub-interface, such as IP address, encapsulation type, and VLAN tagging. |
| description [interface description] | command is used in Cisco IOS to add a description to a specific interface. This description is a text string that can help network administrators identify and understand the purpose or function of the interface. It does not affect the operation of the interface itself but can be useful for documentation and troubleshooting purposes. |
| encapsulation dot1Q [VLAN ID] | used to configure the encapsulation method for a sub-interface on a Cisco router. Specifically, it specifies that the sub-interface will use IEEE 802.1Q encapsulation for VLAN tagging, where “ID” refers to the VLAN ID number. This command is typically used when configuring router-on-a-stick scenarios, where a single physical interface is used to route traffic for multiple VLANs by creating multiple logical sub-interfaces, each associated with a specific VLAN using dot1Q encapsulation. |
| switchport mode trunk | is used to configure an interface on a Cisco switch to operate in trunk mode. In trunk mode, the interface is capable of carrying traffic for multiple VLANs simultaneously. This command allows the interface to send and receive traffic with VLAN tags, enabling it to interconnect switches or routers and carry traffic for multiple VLANs across a single link. |
| switchport trunk allowed vlan ID | is used to specify which VLANs are allowed to traverse a trunk port on a Cisco switch. By default, all VLANs are allowed on a trunk port. However, this command can be used to restrict the VLANs that are permitted to pass through the trunk link. You can specify individual VLAN IDs or specify a range of VLAN IDs that are permitted on the trunk port. |
| show interfaces [interface-ID] switchport | is used to display detailed information about the switchport configuration of a specific interface on a Cisco switch. It provides information such as the administrative and operational mode of the switchport, the VLAN membership of the switchport, trunking status, allowed VLANs, native VLAN, and other relevant details related to the switchport configuration. |
| show interfaces trunk | displays information about trunk interfaces and their associated VLANs. It provides details about which interfaces are configured as trunk links, the encapsulation type (such as dot1Q), the operational status of the trunk, the allowed VLANs on the trunk, and the native VLAN. This command is useful for verifying trunk configurations and troubleshooting trunking issues on Cisco switches. |
| vlan [vlan-id] | used to create a new VLAN with the specified VLAN ID. This command allows network administrators to segment the network into multiple virtual LANs (VLANs) for better traffic management and security. By assigning devices to different VLANs based on their network requirements, administrators can control broadcast domains, enforce security policies, and optimize network performance. |
| switchport mode access | used on Cisco switches to configure an interface as an access port. Access ports are used to connect end devices, such as computers or printers, to the switch. When configured as an access port, the switch treats all incoming frames on that interface as belonging to the VLAN assigned to the port. This command disables dynamic trunking protocol (DTP) negotiation on the interface, ensuring that it operates only as an access port and does not participate in VLAN trunking. |
| switchport access vlan [VLAN-ID] | used on Cisco switches to assign a specific VLAN to an access port. This command is typically used in conjunction with the “switchport mode access” command to configure an interface as an access port and specify the VLAN to which it belongs. By assigning a VLAN to an access port, the switch ensures that all incoming traffic on that port is tagged with the specified VLAN ID. This allows the switch to segregate traffic from different VLANs and control broadcast and multicast traffic within each VLAN. |
| show vlan brief | used on Cisco switches to display a summary of VLAN information. When you enter this command in the CLI interface of a Cisco switch, it provides a concise overview of the VLAN configuration on the switch. This includes details such as the VLAN ID, name, and interface membership status. The output of this command is often used to quickly verify the VLAN configuration and interface assignments on the switch. |
| ipconfig /all | used in Windows operating systems to display detailed information about all network interfaces and their configurations. |
| no shutdown | enables an interface. |
| show running-config | save the running configuration to the startup-configuration file. |
| end | exit configuration mode. |
| exit | exits one level in the menu structure command. |
Lab Task:
- Connect the devices according to the provided topology.
- Connect to the CLI of the routers and enable privileged EXEC mode and go to configuration mode. Configure the appropriate hostname on each device as per topology shown above.
- On Router1, create a loopback interface 100 and assign this IP address 8.8.8.8/32. Explain the use of a Loopback Interface.
- You have been tasked to allocate address blocks for six departments employing the smallest available block for each department. Please utilize this address 192.168.0.0/24 CIDR block from the Request For Comments (RFC) 1918 Class C private address space:
- You will need to document the following attributes:
- Department
- Network Address
- Broadcast Address
- Maximum number of hosts
- First Host
- Last Host
- CIDR Notation
- The network topology consists of a headquarter and a couple of branches. The company has the following departments and each department requires a specific number of hosts:
- Engineering Department – requires 100 hosts
- Human Resources Department – requires 6 hosts
- IT Department – requires 6 hosts
- Production Department – requires 55 hosts
- Finance Department – requires 10 hosts
- Distribution Department – requires 25 hosts
- You must assign address block with the department that has the largest number of hosts and ending with the department with the smallest number of hosts.
- You must create the smallest block of IP addresses possible while allowing sufficient address to encompass all hosts in each department
- You will need to document the following attributes:
- Create an IPv4 address table that include the default gateway, the IPv4 address and the subnet-mask for each PC. Make sure to follow the following requirements:
- Each odd PC number must use the first usable IP address from the given subnet.
- Each even PC number must use the second available usable IP address from the given subnet.
- Each PC must use the last usable IP address from the given subnet as the default gateway.
- Assign the last usable host address from the given subnet to each sub-interface configured on Router1.
- Create a sub-interface on Router1 interface GigabitEthernet0/0/1 for each department and assign the relevant IP address, use the information from step 4 and 5 shown above don’t forget to enable the interface:
- Sub-interface Gig0/0/1.100 -> Engineering Department
- Sub-interface Gig0/0/1.200 -> Human Resources Department
- Sub-interface Gig0/0/1.300 -> IT Department
- Sub-interface Gig0/0/1.400 -> Production Department
- Sub-interface Gig0/0/1.500 -> Finance Department
- Sub-interface Gig0/0/1.600 -> Distribution Department
- Configure sub-interfaces on the router’s trunk interface for each VLAN, specifying the VLAN ID and encapsulation type (dot1q).
- Assign IPv4 addresses on each sub-interface on Router1
- Configure the switch port connected to the router as a trunk port on Switch1. Ensure that VLANs are allowed to pass through the trunk port. Verify that all the VLANs in question are allowed through the trunk.
- Create all the VLANs that are assigned to each department from the “Switch1 VLAN Table” and name each VLAN accordingly.
- On Switch1 set all ports with the appropriate VLAN. Make sure that each interface is set to access mode only. Verify that configuration has been implemented accordingly.
- Assign IPv4 addresses, subnet-mask and default gateway on each PC in the network.
- Verify connectivity between each host with default gateway and 8.8.8.8 IP address which is the loopback interface 100 on Router1.
- Save the configuration across all network devices once everything is working.
Lab Solution:
1- Subnet-Mask Calculator:
| CIDR Notation | Bits | Max Network | Max Hosts | Subnet-Mask |
| 32 | 0 | 1 | 0 | 255.255.255.255 |
| 31 | 1 | 2 | 0 | 255.255.255.254 |
| 30 | 2 | 4 | 2 | 255.255.255.252 |
| 29 | 3 | 8 | 6 | 255.255.255.248 |
| 28 | 4 | 16 | 14 | 255.255.255.240 |
| 27 | 5 | 32 | 30 | 255.255.255.224 |
| 26 | 6 | 64 | 62 | 255.255.255.192 |
| 25 | 7 | 128 | 126 | 255.255.255.128 |
| 24 | 8 | 256 | 254 | 255.255.255.0 |
| 23 | 9 | 512 | 510 | 255.255.254.0 |
| 22 | 10 | 1024 | 1022 | 255.255.252.0 |
| 21 | 11 | 2048 | 2046 | 255.255.248.0 |
| 20 | 12 | 4096 | 4094 | 255.255.240.0 |
| 19 | 13 | 8192 | 8190 | 255.255.224.0 |
| 18 | 14 | 16384 | 16382 | 255.255.192.0 |
| 17 | 15 | 32768 | 32766 | 255.255.128.0 |
| 16 | 16 | 65536 | 65534 | 255.255.0.0 |
The above table is the subnet-mask calculator which simplifies the how to perform subnetting using IPv4 addresses.
The “CIDR Notation” column represent the number of bits of the IP address are used to represent the network. CIDR stands for Classless Inter-Domain Routing notation and it is a compact representation used to express IP address ranges and their associated subnet mask. It simplifies the representation of network addresses by combining the IP address with the number of leading bits that are used to identify the network portion.
The “Bits” column represents the number of bits that will be counting in binary in the IP address or the Mask.
The “Max Network” column is used to identify the number of networks that you can have based on the subnet-mask.
The “Max Hosts” column is the maximum number of hosts that are available for the given subnet-mask.
The “Subnet-mask” column is the subnet-mask expressed in dotted-decimal notation, which is consists of four octets separated by periods. Each octet represents 8 bits of the 32-bit subnet mask, with values ranging from 0 to 255. In binary form, a subnet mask with all 1s in the network portion and all 0s in the host portion represents a network address. For example, a subnet mask of 255.255.255.0 (or /24 in CIDR notation) indicates that the first 24 bits of the IP address represent the network portion, while the remaining 8 bits represent the host portion. This allows for up to 254 hosts per subnet in IPv4.
2- Configuration Steps:
1. Connect Lab Devices: Connect the devices according to the provided topology.
2. Change the name of both routers switches according to the topology:
On Router 1:
Router> enable
Router# configure terminal
Router(config)# hostname Router1
On Switch1:
Switch> enable
Switch# configure terminal
Switch(config)#hostname Switch1
3. Create a loopback 100 interface on Router1:
Configure IPv4 address:
Router1(config)#interface loopback 100
Router1(config-if)#ip address 8.8.8.8 255.255.255.255
b. A loopback interface on a Cisco device is a virtual interface that is used primarily for internal testing, diagnostics, and management purposes. It is a logical interface that does not physically connect to any external network device. Here are some common uses of loopback interfaces on Cisco devices:
a. Device Management: Loopback interfaces provide a stable and reliable source IP address for device management tasks such as SSH, Telnet, SNMP, or management protocols like Syslog and NetFlow. Using a loopback interface ensures that management functions are not affected by changes in physical interfaces or routing configurations.
b. Routing Protocols: Loopback interfaces are often used as the source interface for routing protocol updates, such as OSPF or BGP. Using a loopback interface as the source ensures that routing updates are sent from a stable, always-available IP address, enhancing network stability and resilience.
c. High Availability: In redundant network configurations, loopback interfaces can be used to provide a virtual IP address for services such as HSRP (Hot Standby Router Protocol) or VRRP (Virtual Router Redundancy Protocol). This virtual IP address floats between active and standby devices, allowing for seamless failover without changing the IP addresses of the services.
d. Testing and Troubleshooting: Loopback interfaces can be used for testing connectivity between devices within the same device or network segment. They can also be used to simulate network services or to test the operation of routing protocols without affecting production traffic.
Overall, loopback interfaces offer flexibility, reliability, and ease of management in network configurations, making them a valuable tool for network administrators and engineers.
4. To solve this task, we will need to refer back to the subnet calculator table above:
a. Create a table with the following headers:
b. Assign the subnet for each department, we will start assigning subnets in an ascending order:
1. Engineering department – 100 Hosts
2. Production department – 55 Hosts
3. Distribution department – 25 Hosts
4. Finance department – 10 Hosts
5. HR department – 6 Hosts
6. IT department – 6 Hosts
c. See step 4.b
d. Here is the table for each network per department:
Department table for IPv4 Class C allocation based on 192.168.0.0/24 private address:
| Department Name | Network Address | Broadcast Address | Maximum number of hosts | First host | Last host | CIDR notation |
| Engineering | 192.168.0.0 | 192.168.0.127 | 126 | 192.168.0.1 | 192.168.0.126 | 25 |
| Production | 192.168.0.128 | 192.168.0.191 | 62 | 192.168.0.129 | 192.168.0.190 | 26 |
| Distribution | 192.168.0.192 | 192.168.0.223 | 30 | 192.168.0.193 | 192.168.0.222 | 27 |
| Finance | 192.168.0.224 | 192.168.0.239 | 14 | 192.168.0.225 | 192.168.0.238 | 28 |
| HR | 192.168.0.240 | 192.168.0.247 | 6 | 192.168.0.241 | 192.168.0.246 | 29 |
| IT | 192.168.0.248 | 192.168.0.255 | 6 | 192.168.0.249 | 192.168.0.254 | 29 |
5. IPv4 address table for Router1 and all hosts:
a. For Router1:
| Device Name | Interface ID | IPv4 Address | Subnet-Mask | Department |
| Router 1 | Loopback100 | 8.8.8.8 | 255.255.255.255 | N/A |
| Router 1 | GigabitEthernet0/0/0.100 | 192.168.0.126 | 255.255.255.128 | Engineering |
| Router 1 | GigabitEthernet0/0/0.200 | 192.168.0.246 | 255.255.255.248 | HR |
| Router 1 | GigabitEthernet0/0/0.300 | 192.168.0.254 | 255.255.255.248 | IT |
| Router 1 | GigabitEthernet0/0/0.400 | 192.168.0.190 | 255.255.255.192 | Production |
| Router 1 | GigabitEthernet0/0/0.500 | 192.168.0.238 | 255.255.255.240 | Finance |
| Router 1 | GigabitEthernet0/0/0.600 | 192.168.0.222 | 255.255.255.224 | Distribution |
b. For all hosts:
| Device Name | Department | Interface ID | IPv4 Address | Subnet-Mask | Default Gateway | CIDR Notation |
| PC1 | Engineering | Fa0 | 192.168.0.1 | 255.255.255.128 | 192.168.0.126 | 25 |
| PC2 | Engineering | Fa0 | 192.168.0.2 | 255.255.255.128 | 192.168.0.126 | 25 |
| PC3 | HR | Fa0 | 192.168.0.241 | 255.255.255.248 | 192.168.0.246 | 29 |
| PC4 | HR | Fa0 | 192.168.0.242 | 255.255.255.248 | 192.168.0.246 | 29 |
| PC5 | IT | Fa0 | 192.168.0.249 | 255.255.255.248 | 192.168.0.254 | 29 |
| PC6 | IT | Fa0 | 192.168.0.250 | 255.255.255.248 | 192.168.0.254 | 29 |
| PC7 | Production | Fa0 | 192.168.0.129 | 255.255.255.192 | 192.168.0.190 | 26 |
| PC8 | Production | Fa0 | 192.168.0.130 | 255.255.255.192 | 192.168.0.190 | 26 |
| PC9 | Finance | Fa0 | 192.168.0.225 | 255.255.255.240 | 192.168.0.238 | 28 |
| PC10 | Finance | Fa0 | 192.168.0.226 | 255.255.255.240 | 192.168.0.238 | 28 |
| PC11 | Distribution | Fa0 | 192.168.0.193 | 255.255.255.224 | 192.168.0.222 | 27 |
| PC12 | Distribution | Fa0 | 192.168.0.194 | 255.255.255.224 | 192.168.0.222 | 27 |
6. Create sub-interfaces on Router1:
Router1(config)#interface gigabitEthernet 0/0/1
Router1(config-if)#description “Link to Switch1”
Router1(config-if)#no shutdown
a. Engineering department:
Router1(config-if)#interface gigabitEthernet 0/0/1.100
Router1(config-subif)#description “Engineering Department”
Router1(config-subif)#encapsulation dot1Q 100
Router1(config-subif)#ip address 192.168.0.126 255.255.255.128
b. Human Resources department:
Router1(config)#interface gigabitEthernet 0/0/1.200
Router1(config-subif)#description “Human Resrouces Department”
Router1(config-subif)#encapsulation dot1Q 200
Router1(config-subif)#ip address 192.168.0.246 255.255.255.248
c. IT department:
Router1(config-subif)#interface gigabitEthernet 0/0/1.300
Router1(config-subif)#description “IT Department”
Router1(config-subif)#encapsulation dot1Q 300
Router1(config-subif)#ip address 192.168.0.254 255.255.255.248
d. Production department:
Router1(config-subif)#interface gigabitEthernet 0/0/1.400
Router1(config-subif)#description “Production Department”
Router1(config-subif)#encapsulation dot1Q 400
Router1(config-subif)#ip address 192.168.0.190 255.255.255.192
e. Finance department:
Router1(config-subif)#interface gigabitEthernet 0/0/1.500
Router1(config-subif)#description “Finance Department”
Router1(config-subif)#encapsulation dot1Q 500
Router1(config-subif)#ip address 192.168.0.238 255.255.255.240
f. Distribution department:
Router1(config-subif)#interface gigabitEthernet 0/0/1.600
Router1(config-subif)#description “Distribution Department”
Router1(config-subif)#encapsulation dot1Q 600
Router1(config-subif)#ip address 192.168.0.222 255.255.255.224
7. To configure interface GigabitEthernet0/1 as a trunk on Switch1, you can issue the commands below:
a. Configure port gig0/1:
Switch1#configure terminal
Switch1(config)#interface gigabitEthernet 0/1
Switch1(config-if)#description “Link to Router1”
Switch1(config-if)#switchport mode trunk
Switch1(config-if)#switchport trunk allowed vlan 100,200,300,400,500,600
b. Issue the following command to:
Switch1#show interfaces gigabitEthernet 0/1 switchport
Name: Gig0/1
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: trunk
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Trunking VLANs Enabled: 100,200,300,400,500,600
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Unknown unicast blocked: disabled
Unknown multicast blocked: disabled
Appliance trust: none
Switch1#
Switch1#show interfaces trunk
Port Mode Encapsulation Status Native vlan
Gig0/1 on 802.1q trunking 1
Port Vlans allowed on trunk
Gig0/1 100,200,300,400,500,600
Port Vlans allowed and active in management domain
Gig0/1 100,200,300,400,500,600
Port Vlans in spanning tree forwarding state and not pruned
Gig0/1 100,200,300,400,500,600
Switch1#
8. Create all VLANs on Switch1:
Switch1(config)#vlan 100
Switch1(config-vlan)#name “Engineering Department”
Switch1(config-vlan)#vlan 200
Switch1(config-vlan)#name “Human Resources Department”
Switch1(config-vlan)#vlan 300
Switch1(config-vlan)#name “IT Department”
Switch1(config-vlan)#vlan 400
Switch1(config-vlan)#name “Production Department”
Switch1(config-vlan)#vlan 500
Switch1(config-vlan)#name “Finance Department”
Switch1(config-vlan)#vlan 600
Switch1(config-vlan)#name “Distribution Department”
9. Set all ports on Switch1 with the appropriate VLAN, you can issue the following command to achieve this task:
Switch1(config)#interface range fastEthernet 0/1-2
Switch1(config-if-range)#description “Enginnering Department”
Switch1(config-if-range)#switchport mode access
Switch1(config-if-range)#switchport access vlan 100
Switch1(config-if-range)#
Switch1(config-if-range)#interface range fastEthernet 0/3-4
Switch1(config-if-range)#description “Human Resrouces Department”
Switch1(config-if-range)#switchport mode access
Switch1(config-if-range)#switchport access vlan 200
Switch1(config-if-range)#
Switch1(config-if-range)#interface range fastEthernet 0/5-6
Switch1(config-if-range)#description “IT Department”
Switch1(config-if-range)#switchport mode access
Switch1(config-if-range)#switchport access vlan 300
Switch1(config-if-range)#
Switch1(config-if-range)#interface range fastEthernet 0/7-8
Switch1(config-if-range)#description “Production Department”
Switch1(config-if-range)#switchport mode access
Switch1(config-if-range)#switchport access vlan 400
Switch1(config-if-range)#
Switch1(config-if-range)#interface range fastEthernet 0/9-10
Switch1(config-if-range)#description “Finance Department”
Switch1(config-if-range)#switchport mode access
Switch1(config-if-range)#switchport access vlan 500
Switch1(config-if-range)#
Switch1(config-if-range)#interface range fastEthernet 0/11-12
Switch1(config-if-range)#description “Distribution Department”
Switch1(config-if-range)#switchport mode access
Switch1(config-if-range)#switchport access vlan 600
Switch1(config-if-range)#end
To verify the configuration above, you can issue the command below:
Switch1#show vlan brief
VLAN Name Status Ports
1 default active Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/2
100 Engineering Department active Fa0/1, Fa0/2
200 Human Resources Department active Fa0/3, Fa0/4
300 IT Department active Fa0/5, Fa0/6
400 Production Department active Fa0/7, Fa0/8
500 Finance Department active Fa0/9, Fa0/10
600 Distribution Department active Fa0/11, Fa0/12
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
Switch1#
10. Assign the appropriate IP address per PC:
a. PC1:

b. PC2:

c. PC3:

d. PC4:

e. PC5:

f. PC6:

g. PC7:

h. PC8:

i. PC9:

j. PC10:

k. PC11:

l. PC12:

11. Connectivity verification:
a. PC1:

b. PC2:

c. PC3:

d. PC4:

e. PC5:

f. PC6:

g. PC7:

h. PC8:

i. PC9:

j. PC10:

k. PC11:

l. PC12:

12. Save the configuration by issuing either “wr” or “copy running-config startup-config” command on all Cisco devices.
Troubleshooting:
- If ping fails, double-check IP addressing, subnet masks, default gateways, switch and router configurations.
- Ensure that routing is correctly configured to allow traffic between subnets.
- Ensure Each PC is in the correct VLAN and that each VLAN is allowed throughout the trunk link between Switch1 and Router1.
Note:
Variable Length Subnet Masking (VLSM) is a technique used in IP addressing to allocate IP addresses based on network requirements more efficiently. Here’s a detailed overview:
- Traditional Subnetting vs. VLSM:
- In traditional subnetting, all subnets within a network have the same subnet mask, leading to wastage of IP addresses.
- VLSM allows the use of different subnet masks within the same network, enabling better utilization of IP addresses.
- Usage:
- VLSM is commonly used in large networks, such as enterprises, ISPs, and data centres, where efficient IP address allocation is crucial.
- Benefits:
- Maximizes IP address utilization: Allows subnetting to occur with varying sizes based on the specific needs of each subnet, reducing IP address wastage.
- Scalability: Enables networks to grow organically without the need for major restructuring of IP addresses.
- Efficient use of routing tables: Helps in reducing the size of routing tables by aggregating smaller subnets into larger ones.
- Implementation:
- VLSM is implemented by dividing an IP address space into smaller subnets with different subnet masks.
- Subnet masks are assigned based on the number of host addresses required in each subnet, with larger subnets getting smaller masks (more hosts) and vice versa.
- Example:
- Suppose you have a network with IP address 192.168.1.0/24 (Class C).
- Using VLSM, you can divide this network into smaller subnets, such as:
- Subnet 1: 192.168.1.0/26 (64 hosts)
- Subnet 2: 192.168.1.64/27 (32 hosts)
- Subnet 3: 192.168.1.96/28 (16 hosts)
- This allows each subnet to have a different number of hosts based on its requirements.
- Routing:
- VLSM requires support from routing protocols like RIPv2, EIGRP, OSPF, or BGP, which must advertise subnet masks along with IP routes.
- It allows routers to route traffic more efficiently by using the most specific route available.
Conclusion:
Through this lab, you’ve practiced VLSM subnetting and gained practical experience in configuring routers and PCs in a subnetted network. Understanding VLSM is essential for efficient IP address allocation and network design. Keep exploring and practicing to reinforce your networking skills!
Packet Tracer Lab (Pre/Post configuration):
Download the file below and open the word document to access the Packet Tracer labs.