Lab 006 Understand Basics Configurations on a Router
Watch Full Demo on YouTube:
Lab Objective:
The objective of this lab is to configure a Cisco router with essential settings to ensure proper network operation and security. When setting up a new network environment or a new office you must configure the router with essential configuration for operation and security.
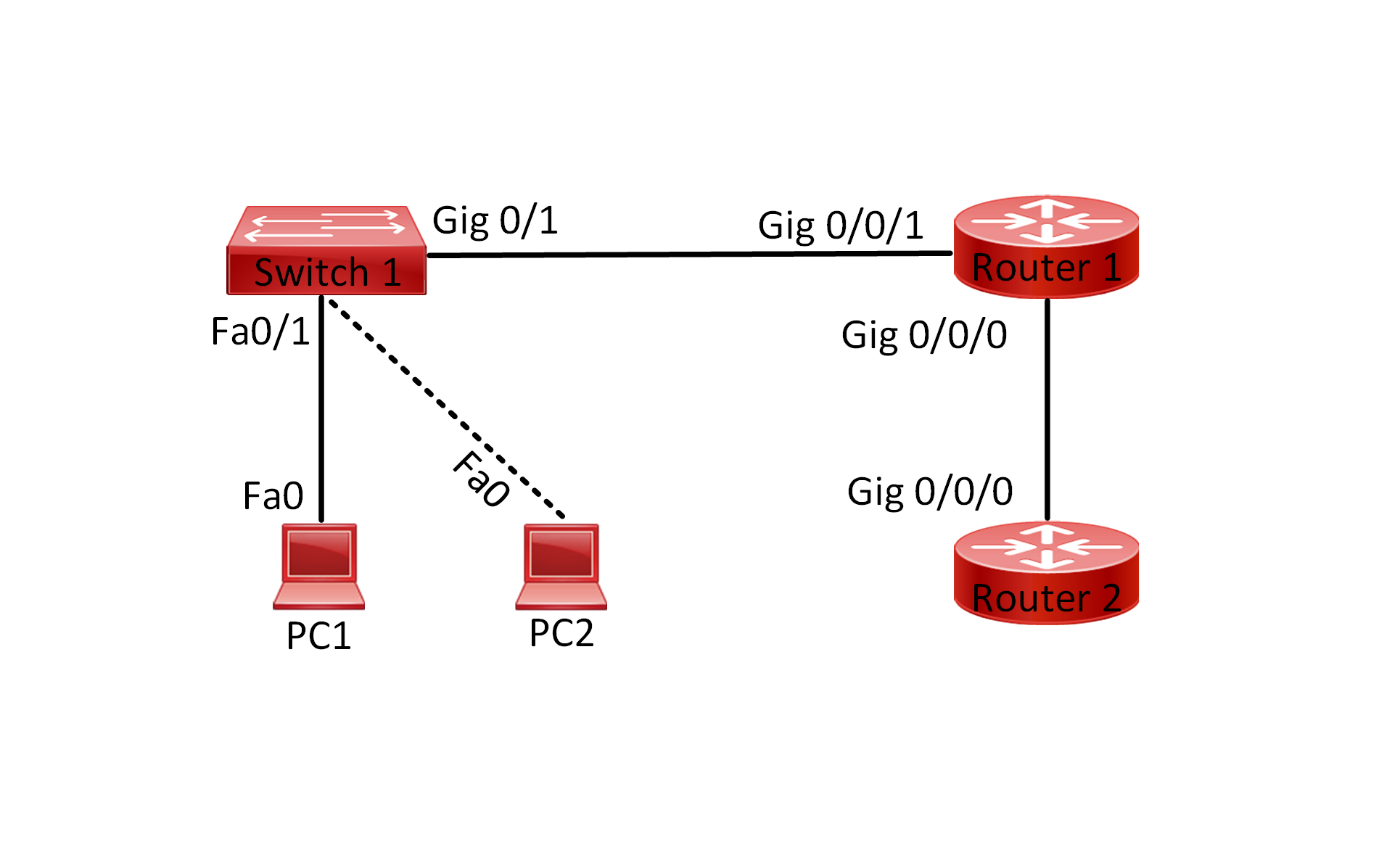
Lab Topology:

Equipment Required:
- 2x Cisco Router
- Console Cable
- Ethernet Cable
- Computer with Terminal emulation software e.g. PuTTY
IPv4 Address Table:
| Device Name | Interface ID | IPv4 Address | Subnet-Mask |
| Router 1 | GigabitEthernet0/0/1 | 172.16.0.1/30 | 255.255.255.252 |
| Router 2 | GigabitEthernet0/0/2 | 172.16.0.2/30 | 255.255.255.252 |
List of Command Summary:
| Command | Command Description |
| enable | enters privileged EXEC mode. |
| configure terminal | enters global configuration mode from privileged EXEC mode. |
| hostname [hostname] | Assign a device name to router. |
| enable password [password word] | Sets a password for privileged EXEC mode (this password is not encrypted) |
| enable secret [password word] | Sets an encrypted password for privileged EXEC mode |
| service password-encryption | used in Cisco IOS to encrypt plaintext passwords stored in the router’s running configuration. When this command is enabled, any plaintext passwords configured on the router (such as console, enable, and user passwords) will be encrypted using a weak encryption algorithm known as Type 7 |
| banner motd [delimiter] [message] [delimiter] | Configures a MOTD banner |
| banner login [delimiter] [message] [delimiter] | Configures a login banner. |
| interface [type number] | Change from global configuration mode to interface configuration mode. |
| description [interface description] | command is used in Cisco IOS to add a description to a specific interface. This description is a text string that can help network administrators identify and understand the purpose or function of the interface. It does not affect the operation of the interface itself but can be useful for documentation and troubleshooting purposes |
| no shutdown | enables an interface. |
| line console 0 | Enters console line configuration mode |
| line vty [first line number] [last line number] | Enters VTY line configuration mode |
| login local | Enables login authentication on the console or VTY lines |
| exec-timeout [number of minutes] [number of seconds] | used to set the maximum amount of time a user session can remain inactive before it automatically terminates |
| logging synchronous | used to prevent console messages from interrupting command entry |
| transport input ssh | Specifies SSH as the transport protocol for VTY lines |
| ip domain-name [domain name] | Configures the router’s domain name for SSH |
| crypto key generate rsa [1024] | Generates RSA keys for SSH |
| ip ssh version 2 | Set SSH protocol to version 2 |
| cdp enable | enables Cisco Discovery Protocol on the interface |
| cdp run | enable CDP globally on the device |
| username [username word] secret 0 [password word] | Creates a local user account and password. |
| username [username word] privilege [user privilege level <0-15>] secret [password word] | Creates a local user account with the specified privilege level and password. |
| no ip domain-lookup | used in Cisco IOS to disable the Domain Name System (DNS) lookup feature on the router |
| show running-config | save the running configuration to the startup-configuration file. |
| show running-config interface [interface-id] | display the current running configuration of a specific interface on a Cisco device. This command provides detailed information about the configuration settings applied to the specified interface, including IP addresses, VLAN assignments, interface status, and any configured parameters such as speed, duplex mode, or access control lists (ACLs) |
| show ip ssh | display information about the SSH server configuration on the router |
| end | exit configuration mode |
| exit | exits one level in the menu structure command |
Lab Task:
- Connect the devices according to the provided topology.
- Connect to the CLI of the routers and enable privileged EXEC mode and go to configuration mode. Configure the appropriate hostname on each device as per topology shown above.
- Configure IPv4 addresses on the appropriate interfaces and enable the following:
- Create the following interface description.
“Link to Router[i]”.
Where i is the instant number of the router. - Enable Cisco discovery protocol on the interface.
- Enable the interface.
- Create the following interface description.
- Examine each interface and initiate a ping for each side and make sure there is connectivity between Router1 and Router2. Explore the following:
- Interface Status
- MAC Address
- Network Address
- Input and output counters
- Interface speed/bandwidth
- From the global config mode configure the following on both routers:
- Create a password for EXEC Mode, please use “Cisco123”
- Enable CDP globally
- Check the running-configuration
- Can you read the enable password?
- Log out and log back in again and go to user EXEC Mode. (You must use the password created at step 5.a)
- From the global config mode configure the following, on both routers:
- Create a secret password for EXEC Mode, please use “IEE123”
- Check the running-config again and check the password configured for each enable command, what do you see?
- Exit the User EXEC mode and try to issue the “enable” command, please use the “Cisco123” password, have you managed to log in? Why the password didn’t work?Use the “IEE123” password to get to the user EXEC Mode.
- Create a local account with a password from the from below:
- Account name: iee
- Password: iee
- Create a local account with the highest privilege level from the below:
- Account name: admin
- Password: admin
- Configure the console interface with the following attributes:
- Set the time to 1 minute and 10 seconds for the session that can remain inactive before it automatically terminates.
- Use the command that prevents console messages from interrupting command entry.
- Enable local authentication for login sessions.
- Exit user privilege mode and exit the user access mode. You should be locked out of the router. At this stage hit enter and login with the “iee” account. Observe the prompt.
- Repeat step “7.d” and use the “admin” account instead.
- What is the different between the prompt you get from each account.
- Configure banners for the following:
- Message of the Day, to use the text below:
banner motd #
WARNING: Unauthorized access prohibited!
# - Login, to use the text below:
banner login #
WARNING: Unauthorized access prohibited! You must have explicit permission to access this device.
# - Repeat step 7.d. Do you see the MOTD and the login banner?
- Message of the Day, to use the text below:
- Configure line vty 0 4 with the following attributes:
- Set the time to 1 minute and 10 seconds for the session that can remain inactive before it automatically terminates.
- Use the command that prevents console messages from interrupting command entry.
- Enable local authentication for login sessions.
- Configure inbound connections to use only SSH protocol.
- Configure SSH version 2, with the following steps:
- Create a new domain name, please use IEE.LOCAL.
- Create an RSA key with 1024 bits.
- Set the SSH version to 2.
- Verify that SSH protocol is being enabled and using version 2.
- Verify that you can SSH to Router2 from Router1 and vice versa.
- Check CDP neighbor command, what can you observe?
- Disable Domain Name System lookup feature on the router.
- Save the configuration across all network devices once everything is working.
Configuration Steps:
1. Connect Lab Devices: Connect the devices according to the provided topology.
2. Change the name of both routers switches according to the topology:
a. On Router 1:
Router> enable
Router# configure terminal
Router(config)# hostname Router1
b. On Router 2:
Router> enable
Router# configure terminal
Router(config)# hostname Router2
3. Configure ipv4 address on both routers:
a. Router1:
Router1(config)#interface gigabitEthernet 0/0/1
Router1(config-if)#description “Link to Router2”
Router1(config-if)#ip address 172.16.0.1 255.255.255.252
Router1(config-if)#cdp enable
Router1(config-if)#no shut
b. Router2:
Router2(config)#interface gigabitEthernet 0/0/2
Router2(config-if)#description “Link to Router1”
Router2(config-if)#ip address 172.16.0.2 255.255.255.252
Router2(config-if)#cdp enable
Router2(config-if)#no shut
4. Examine each interface and initiate a ping for each side:
a. On Router1:

b. On Router2:

5. From the global configuration mode:
a. Create a password for the EXEC Mode:
a. On Router1:
Router1(config)#enable password Cisco123
b. On Router2:
Router2(config)#enable password Cisco123
b. Enable CDP Globally:
a. On Router1:
Router1(config)#cdp run
b. On Router2:
Router2(config)#cdp run
c. Issue “show running-config”:
a. On Router1:

b. On Router2:

d. Yes, you can read the password in plain text
e. Log out from the CLI and log back in, when we execute the enable command, we must use the password we just created.
6. From the global config mode configure the following:
a. On Router1:
a. Create a secret password:
Router1(config)#enable secret IEE123
b. Check the running config again and check the password configured for each enable command:

c. When both are configured, the router will use the “enable secret” password for authentication, effectively overriding the “enable password”. This is because the “enable secret” password is encrypted using a stronger encryption algorithm compared to the “enable password”, making it more resistant to unauthorized access. Therefore, even if both passwords are configured, only the “enable secret” password will be used for authentication purposes.
d. We must use the “IEE123” password.
e. The “service password-encryption” command is used to encrypt plain text passwords stored in the router’s configuration. When this command is enabled, any passwords configured on the router, such as console, telnet, or enable passwords, are encrypted and displayed as ciphertext in the configuration file. This helps enhance security by preventing someone from easily viewing the passwords in plaintext if they gain access to the router’s configuration. However, it’s important to note that this encryption method is relatively weak and can be easily decrypted using readily available tools, so it’s not considered a robust security measure on its own.
Router1(config)#service password-encryption
f. Create a local account:
Router1(config)#username iee password 0 iee
b. On Router2:
a. Create a secret password:
Router2(config)#enable secret IEE123
b. Check the running config again and check the password configured for each enable command:

c. When both are configured, the router will use the “enable secret” password for authentication, effectively overriding the “enable password”. This is because the “enable secret” password is encrypted using a stronger encryption algorithm compared to the “enable password”, making it more resistant to unauthorized access. Therefore, even if both passwords are configured, only the “enable secret” password will be used for authentication purposes.
d. We must use the “IEE123” password.
e. The “service password-encryption” command is used to encrypt plain text passwords stored in the router’s configuration. When this command is enabled, any passwords configured on the router, such as console, telnet, or enable passwords, are encrypted and displayed as ciphertext in the configuration file. This helps enhance security by preventing someone from easily viewing the passwords in plaintext if they gain access to the router’s configuration. However, it’s important to note that this encryption method is relatively weak and can be easily decrypted using readily available tools, so it’s not considered a robust security measure on its own.
Router1(config)#service password-encryption
f. Create a local account:
Router1(config)#username iee password 0 iee
g. Create a local account with the highest privilege:
Router1(config)#username admin privilege 15 secret admin
7. Configure console interface:
a. On Router1:
a. Use the following command to set the inactive console session for 1 minute and 10 seconds:
Router1(config)#line console 0
Router1(config-line)#exec-timeout 1 10
b. Issue the following command:
Router1(config-line)#logging synchronous
c. Enable local authentication:
Router1(config-line)#login local
d. Logged in successfully with the “iee” account however we were prompted with user access mode:

e. Logged in successfully with the “admin” account and we were prompted with EXEC Privileged mode

f. The difference between using the “iee” and the “admin” accounts is that the “admin” account has been set with privilege level 15 which means, once the user is authenticated can go directly onto user EXEC mode
b. On Router2:
a. Use the following command to set the inactive console session for 1 minute and 10 seconds:
Router2(config)#line console 0
Router2(config-line)#exec-timeout 1 10
b. Issue the following command:
Router2(config-line)#logging synchronous
c. Enable local authentication:
Router2(config-line)#login local
d. Logged in successfully with the “iee” account however we were prompted with user access mode:

e. Logged in successfully with the “admin” account and we were prompted with EXEC Privileged mode:

f. The difference between using the “iee” and the “admin” accounts is that the “admin” account has been set with privilege level 15 which means, once the user is authenticated can go directly onto user EXEC mode
8. Banner configuration shown below:
a. On Router1:
a. Banner MOTD:
Router1(config)#banner motd #
WARNING: Unauthorized access prohibited!
#
Router1(config)#
b. Banner Login:
Router1(config)#banner login #
WARNING: Unauthorized access prohibited! You must have explicit permission to access this device.
#
Router1(config)#
c. Login back to the router, you can see the new prompt:

a. On Router2:
a. Banner MOTD:
Router2(config)#banner motd #
WARNING: Unauthorized access prohibited!
#
Router2(config)#
b. Banner Login:
Router2(config)#banner login #
WARNING: Unauthorized access prohibited! You must have explicit permission to access this device.
#
Router2(config)#
c. Login back to the router, you can see the new prompt:

9. The below is the config for line vty 0 4:
a. On Router1:
Use the following command to set the time:
Router1(config)#line vty 0 4
Router1(config-line)#exec-timeout 1 10
Issue the command below:
Router1(config-line)#logging synchronous
Enable local authentication:
Router1(config-line)#login local
Configure inbound connections to use only SSH v2:
Router1(config-line)#transport input ssh
b. On Router2:
Use the following command to set the time:
Router2(config)#line vty 0 4
Router2(config-line)#exec-timeout 1 10
Issue the command below:
Router2(config-line)#logging synchronous
Enable local authentication:
Router2(config-line)#login local
Configure inbound connections to use only SSH v2:
Router2(config-line)#transport input ssh
10. Configure SSHv2:
a. On Router1:
Create a new domain:
Router1(config)#ip domain-name IEE.LOCAL
Create an RSA key with 1024 bits:
Router1(config)#crypto key generate rsa
The name for the keys will be: Router1.IEE.LOCAL
Choose the size of the key modulus in the range of 360 to 4096 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable…[OK]
Router1(config)#
Set the SSH version to 2:
Router1(config)#ip ssh version 2
Verification:
Router1#sh ip ssh
SSH Enabled – version 2.0
Authentication timeout: 120 secs; Authentication retries: 3
Router1#
b. On Router2:
Create a new domain:
Router2(config)#ip domain-name IEE.LOCAL
Create an RSA key with 1024 bits:
Router2(config)#crypto key generate rsa
The name for the keys will be: Router2.IEE.LOCAL
Choose the size of the key modulus in the range of 360 to 4096 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable…[OK]
Router2(config)#
Set the SSH version to 2:
Router2(config)#ip ssh version 2
Verification:
Router2#show ip ssh
SSH Enabled – version 2.0
Authentication timeout: 120 secs; Authentication retries: 3
Router2#
11. SSH verification between Router1 and Router2 and vice versa:
a. On Router1:

b. On Router2:

12. To check the neigboring device we need to use the following command:
a. On Router1:

b. On Router2:

13. To disable the Domain Name System lookup feature issue the command below:
a. On Router1:
Router1(config)#no ip domain-lookup
b. On Router2:
Router2(config)#no ip domain-lookup
14. Save the configuration by issuing wr command.
Conclusion:
In this lab, we successfully configured essential settings on Cisco routers, including IPv4 addresses, interface descriptions, CDP, basic security measures, and banners. These configurations ensure proper network operation and enhance security on the routers.
Packet Tracer Lab (Pre/Post configuration):
Download the file below and open the word document to access the Packet Tracer labs.